
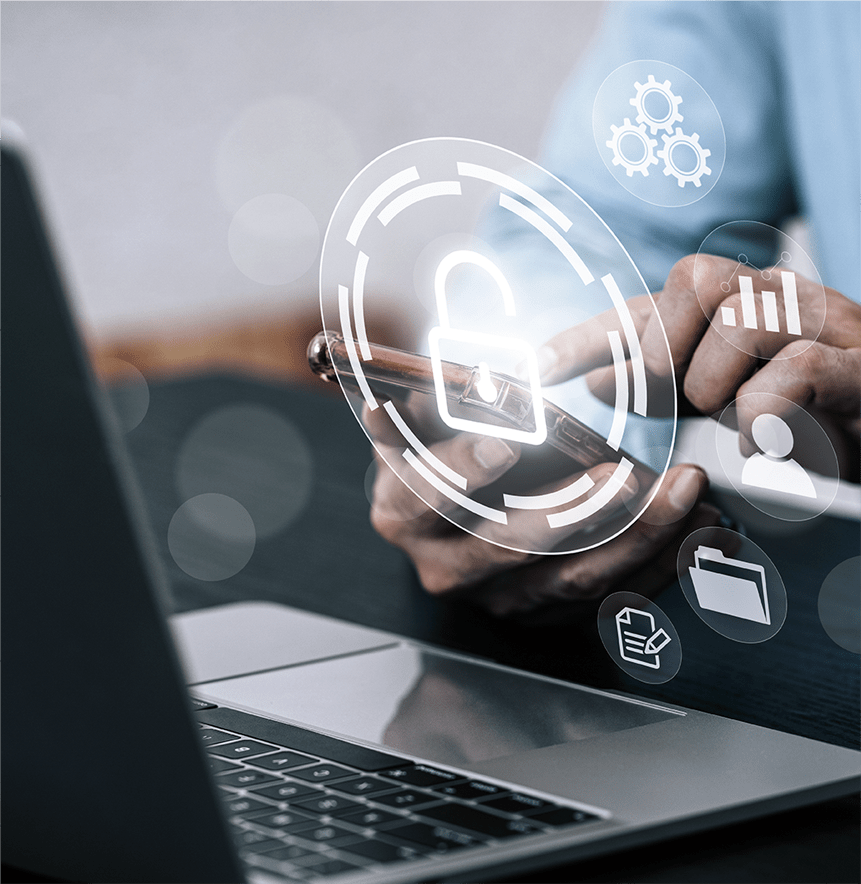
Put in the hands of specialists the security of your information, to protect devices, electronic systems, servers, networks. In case of any cyber-attack, hacking, damage, or unauthorized access.
In Orion IT Solutions and Services, we have certified engineers in computer security to protect your equipment, networks, software applications, critical systems, and data from possible digital threats to keep your company safe from cyber-attacks.
Among the measures we implement are the configuration of security software, firewall devices, installation of antivirus and antimalware software, protection of sensitive data through encryption, implementation of user authentication, and conducting audits and penetration tests, among others. In addition, we offer constant monitoring and analysis of systems to detect and prevent possible threats.
Information
protection

We protect your company's confidential information, such as customer data, financial and strategic information, among others.
Cyber risk
reduction

We help significantly reduce the risk of cyber-attacks, such as viruses, malware, phishing, and ransomware.
Early threat
detection
We use advanced tools to detect threats early, which helps prevent possible damage to the company.
Access control and authentication

We implement access control and user authentication policies and mechanisms.
At Orión IT Solutions and Services we provide storage to have your databases in the Cloud secure, reliable, and highly available, our service is through a cloud platform.
We carry out the migration of your data in an automated and agile way with a combination of technology, methodology and services. This solution consists of comprehensive, open, and unified data integration technology that enables data migration.
We understand the source database and define the migration strategy.
Evaluate the data
Convert database schema
Test the migration compilation
Execute the migration

Protecting against external hacker attacks

Knowing the risks you are exposed to and strengthening your weaknesses

No need for expensive infrastructure

Allows you to create a plan of action against possible attacks

ncreased efficiency, since information security tools allow you to have total control of what happens to your data.



If you want to be partof this great team, register your data in the form and attach your study plan.